Last Updated on 2 years by admin
Security researcher Saar Amar, found Kernel-level vulnerability in IOMobileFrameBuffer / AppleCLCD. This attack surface is accessible from the app sandbox and it’s great for jailbreaks.
The POC tested in a physical device iPhone X running iOS 14.7.1 and on the virtual device iPhone 11 Pro running iOS 15. Further, he confirmed the POCs work all the same on iOS 14.7.1 – iOS 15.0.1. However, Apple fixed this by releasing iOS 15.0.2.
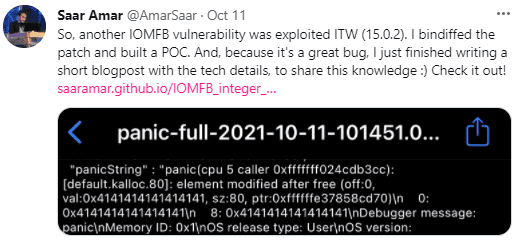
According to Amar, the bug resides in AppleMobileDispH12P, which is accessible from AppleCLCD. After some reversing and a basic understanding of the flow, you can see that this function is accessible from external method 78. This flow is accessible directly from the app sandbox, no special entitlements are required. So, Jailbreak developers can just create an iOS app with his POC, run it on the device and trigger the bug.
Security researcher @pattern_F_ share a video of jailbreak demo built using the kernel vulnerability by Amar
He used an iPhone 11 running iOS 14 to verify the vulnerability is exploitable. He mentioned that the code used in the demo is based on the older ipc_kmsg hack and it has better speed when compared to the cicuta_verosa exploit. But the ipc_kmsg hack doesn’t work on iOS versions beyond iOS 14.2 due to iOS exploit primitive controls. That’s why he couldn’t check any other latest versions.
However, it proves that this vulnerability exists on all iOS 14 – iOS 14.8, iOS 15, iOS 15.0.1 & iOS 15.0.2 versions.
When we talk about iOS 15 Jailbreak, it is necessary additional effort by jailbreak developers. Because of iOS 15 implemented security mitigations.
Also, according to him the original POC will trigger a co-processor fault, other than an API kernel panic on A14 and A15. It needs a lot of reverse engineering. So, it might need additional difficulties jailbreaking on A14 and A15-equipped iPhone 12 and 13 lineups.
Hence there is no proper semi-untethered jailbreak since iOS 14.3. It really needs a real jailbreak tool for iOS 14.4 onwards. In the past couple of months, it has hinted about many iOS vulnerabilities / iOS zero day exploit on these versions. It could create a new jailbreak tool or an upgraded version of Unc0ver or Taurine jailbreak tools.

